Whoa, that’s wild! I opened a Solana transaction and my first reaction was pure curiosity. There was a heap of raw data, hashes, and nested instructions. Initially I thought this would be a quick glance, but then the details kept pulling me in because every instruction could change state and value across several accounts. On one hand the speed of Solana impresses me, though actually I worry about how quickly a confusing transaction can become opaque when you don’t have the right tools to parse program logs and inner instructions.
Seriously? It matters. Sol transactions are fast and cheap compared with many other chains. But that very speed can hide complexity in packed instructions and parallel execution. If you’re tracking token flows or debugging a failed swap you need an explorer that surfaces inner transactions, parsed logs, decoded instruction data, and clear token metadata so you can trace state transitions across programs and accounts. My instinct said a basic explorer would be enough, yet after a few real world incidents I realized surface-level views don’t cut it when program-derived addresses or multisig wallets are involved and you need provenance.
Hmm… this part matters. That’s why explorers like the one I use shine—because they group data into readable segments. You get a breakdown of instructions, fee details, confirmations, and associated token movements. When I first started using Solana analytics tools I would cross-check transactions with wallet addresses and token mints to reconstruct order flow and eventually to attribute trades to likely bots or market makers. Actually, wait—let me rephrase that: it’s less about blame and more about understanding on-chain causality so you can make smarter decisions or craft safer smart contracts that don’t leave edge cases unhandled.
Whoa, check this out— A few weeks ago I saw a failed liquidity add that still moved funds. My instinct said somethin’ was off when the fee patterns didn’t match normal usage. Using detailed logs, inner instruction decoders, and token transfer tables I traced the event to a program anomaly that re-routed lamports through a temporary account, which then triggered a fallback path in a DEX implementation. I’ll be honest, that kind of forensic work is tedious and exciting at the same time because you learn the guts of composable finance and where assumptions break down under load.
Wow! Useful stuff. Sol analytics surface wallet clusters, historical balances, and holder distributions. You can watch trading patterns across token pairs and sometimes spot whale accumulation early. There are dashboards that aggregate activity into visual graphs and heatmaps and, if you set alerts, they can notify you when large transfers or suspicious contract calls occur, helping you act before a market swing. On one hand automatic alerts are lifesavers during volatile times, though on the other hand they can be noisy and require careful tuning or you’ll get desensitized to true incidents.
Mục Lục
Why I rely on solscan explorer
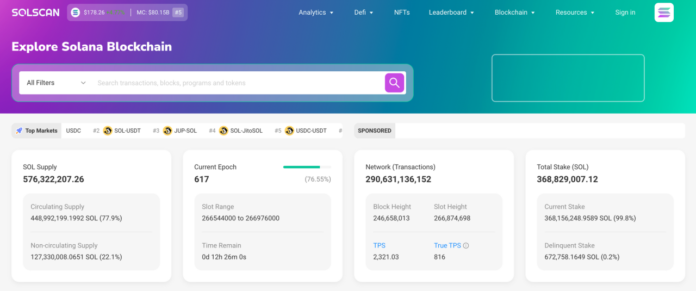
For me the practical difference is in the details, so I regularly open solscan explorer to decode inner instructions and verify token movement quickly and visually.
Hmm. Pro tip: Always cross-reference a transaction’s block time with confirmation status and fee payer details. Check recent signatures for similar instruction patterns then inspect inner logs for program-specific errors. If you’re debugging a wallet integration, don’t stop at the “Success” flag; inspect pre- and post-balances and log messages because program state changes are often subtle and can be masked by rent exemptions or recalculations. Once I missed a tiny rent-exempt delta that caused a retry loop, and I only caught it by comparing ledger snapshots across several blocks which taught me to never assume atomicity in complex multi-instruction transactions.
Seriously, it’s wild. Advanced analytics often hinge on token metadata accuracy and mint authority histories. In practice you map token flows by mint address and then identify clusters by shared activity. Developers use program logs to reconstruct call graphs and to understand how accounts mutate over time, and auditors will simulate transactions locally to reproduce state transitions when investigating vulnerabilities. On one hand these tools empower builders with transparency, though actually they sometimes reveal messy permission models that projects should have designed more carefully from the start.
Okay, so here’s something. For teams, analytics often guide risk management and product UX decisions. You learn which instructions users hit most and where confirmations commonly fail. If you’re shipping a wallet or a dApp, instrumenting analytics endpoints and correlating on-chain events with off-chain telemetry helps you rebuild user sessions and prioritize fixes before complaints escalate. I take pride in building observability into products because when you can answer “why did this user see an error” in ten minutes instead of days you save trust and money, and that matters in competitive markets like the US and global crypto hubs.
Hmm… privacy matters. Remember that blockchain transparency can expose more than you expect about trading habits. Many users anonymize addresses but pattern analysis still links behavior back to clusters. For sensitive operations or payroll flows think about off-chain mixers or custodial abstractions to reduce exposure, and always consider legal implications because on-chain visibility crosses regulatory boundaries depending on jurisdiction. I’m biased, but privacy design should be baked in from day one rather than bolted on after a public leak forces an expensive cleanup and reputational fallout.
Here’s the thing. Good explorers make a difference for traders, devs, and curious users. If you want to inspect Solana transactions in depth, use tools that decode instructions and list all token movements. I often open an explorer before approving a new program interaction, because despite convenience the cost of one mistaken approval can be far greater than a quick five-minute audit on the transaction flow and related accounts. In the end the chain tells a story, and with practice you’ll read it faster—though you’ll still have those moments of surprise when a transaction hides somethin’ clever that only a good explorer can reveal.
FAQ
What should I check first in a Solana transaction?
Start with the fee payer, confirmation status, and block time, then expand to decoded instructions and token transfers; trace pre- and post-balances to understand account state changes.
Can I rely solely on explorers for security audits?
No. Explorers are indispensable for visibility and triage, but formal audits and local transaction simulation are required to confidently prove safety for complex programs.
How do alerts help without creating noise?
Tune thresholds, whitelist important programs, and correlate alerts with off-chain signals so you only escalate incidents that affect users or funds materially.

TS.BS Vũ Trường Khanh có thế mạnh trong điều trị một số bệnh Gan mật như:
- Gan nhiễm mỡ
- Viêm gan do rượu
- Xơ gan
- Ung thư gan…
Kinh nghiệm
- Trưởng khoa Tiêu hóa – Bệnh viện Bạch Mai
- Thành viên Ban thường trực Liên chi hội Nội soi tiêu hóa Việt Nam
- Bác sĩ đầu tiên của Khoa Tiêu hoá ứng dụng phương pháp bắn tiêm xơ tĩnh mạch trong điều trị xơ gan mạn tính
- Bác sĩ Vũ Trường Khanh tham gia tư vấn về bệnh Gan trên nhiều kênh báo chí uy tín: VOV, VnExpress, cafeF…
- Các kiến thức về thuốc điều trị viêm gan hiệu quả